Type: #arbitraryData #validation
Project: Maestro bot
Date: 25/10/23
Blockchain: ETH
Problem: One of the Router functions allows arbitrary calls to the token contract.
This incident was caused by a contract vulnerability that allowed an attacker to transfer any token for which approval had been granted on the Maestro Router2 contract.
Maestro's Router2 contract operates as an ERC1967-like proxy, delegating to its implementation, which handles all the logic for swaps and bribes for block builders.
The attack initiated with a call to function 0x9239127f on the router (`0x80a64...`), which delegated to its implementation (`0x82eae9...`), and allowed the attacker to transfer tokens from users to themselves using the transferFrom method.
Approximately 30 minutes following the initial exploit transaction, Maestro replaced the router's implementation with a dummy Counter contract, effectively halting the router's functionality and preventing further funds from being stolen.
The Hacker:
1) Checked user allowance of tokens to the Router 2 contract.
2) Used 0x9239127f function to call 'transferFrom' (`23b872dd...`) for each user, transferring their to hacker's address. ,
3) Sold all tokens for ETH.
4) Washed the funds through Railgun mixer.
Discoverer: NaN, was hacked
Harm: 500 k $
link
Oct 25, 2023, 12:11 PM

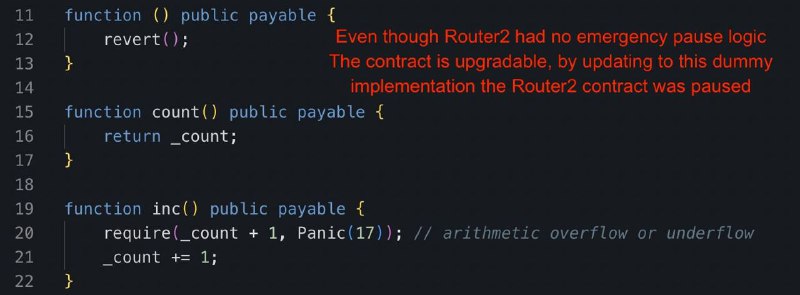
Oct 25, 2023, 12:11 PM
Counters.sol unexpected comeback
Oct 25, 2023, 3:06 PM
