Project: Harpie
Platform: Sherlock
Source, Code
Number: 32
Problem: Signature malleability not protected against
Severity: Medium
Vulnerability detail:
OpenZeppelin has a vulnerability in versions lower than 4.7.3, which can be exploited by an attacker. The project uses a vulnerable version
All of the conditions from the advisory are satisfied: the signature comes in a single bytes argument, ECDSA.recover() is used, and the signatures themselves are used for replay protection checks
oz_vulnerabilitiy
If a user calls changeRecipientAddress(), notices a mistake, then calls changeRecipientAddress() again, an attacker can use signature malleability to re-submit the first change request, as long as the old request has not expired yet.
Impact:
The wrong, potentially now-malicious, address will be the valid change recipient, which could lead to the loss of funds.
Mitigation:
Change oz to version 4.7.3
Fix
#SHERLOCK #REPORT #SIGNATURE #HARPIE
Feb 14, 2023, 1:37 PM
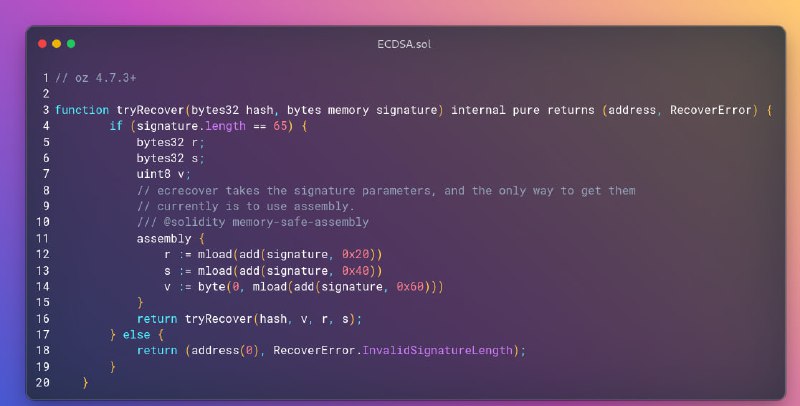
Feb 14, 2023, 1:37 PM
Am I missing something or how exactly is the new oz version protecting signature replay?
Which actually should be fixed by introducing a nonce imo
Feb 14, 2023, 2:04 PM
I added the pics
It lacks the option with length = 64
My understanding of that is if you have some protection from replay attacks and u're using the mapping, you can bypass it with length = 64 signature (signature malleability)
Feb 14, 2023, 2:11 PM
That... still won't prevent it from being reused. Sure it'll prevent usage of different formats, but the exact same signature can be used in replay
Feb 14, 2023, 2:19 PM
We ended the discussion in pm😅🫡
Feb 14, 2023, 2:53 PM
